You were caught! :(
[Polish][English]
Busted!
You have just clicked on a suspicious link and entered your username and password on a fake website!
This time it was just a test initiated by Medicover Group Cyber Security Department. However, if this attack had been real, hackers would have gained access to your logging data that you are using to access to corporate email and other corporate applications. This could have infected your computer and then leaked sensitive data, and consequently exposed the Company to severe losses.
Remember to always double check the sender address. A valid address includes medicover.pl or medicover.com domain name
Example: Surname Name <name.surname@medicover.pl>
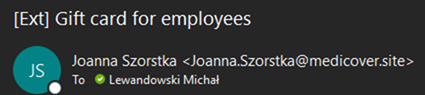
The suspicious address includes: medicover.site domain.
Example: Joanna Szorstka <Joanna.Szorstka@medicover.site>
another example of suspicious address may include: medıcover.com domain, but with "ı" - which pretends to be the letter "i" (no dot)
Example: Security Team security.team@medıcover.com
Additionally, all messages coming from Medicover are sent from our internal servers. The [EXT] at the beginning of the subject line indicates that the message comes from outside of the organisation. Pay special attention if you are prompted to open files, click on a link, and provide credentials in a non-corporate message.
All suspicious messages should be reported to the official Helpdesk email address: helpdesk@medicover.pl
Stay vigilant in the future!
Until the test is completed (2021-11-22), we ask you to keep the result to yourself, we want to give everyone a chance to test their vigilance. The purpose of the test is only to investigate how well we can recognize the risks and prepare for further training.
Survey conducted on behalf of Medicover.
Thank you for taking part in the survey!
 Edukacja - Phisihing
Edukacja - Phisihing